mesaforte®: the GRC tools that protect your business suite
Our GRC software governs and supervises data access to your business suite cost-efficiently. For Microsoft, SAP, and other ERP systems. Try our solution today!
Governance, Risk & Compliance for your business suite
Discover wikima4 mesaforte, a powerful GRC tool suite.
- The SaaS solution with customizable and scalable modules for compliance SOD, IT security and reporting, creates security and optimizes processes.
- mesaforte is SAP® S/4HANA ready and therefore the ideal GRC tool for your company.
- Are you looking for a comprehensive security solution for your ERP or individual modules? We will be happy to support you personally in the evaluation and implementation.
Individual
9 scalable modules for your compliance, control and reporting needs
wikima4 mesaforte.Compliance.Suite runs as a standalone application, accesses the systems with connectors
Quick and easy installation in your environment or available as SaaS (“Software-as-a-Service”)
Cost-effective
Implementation through predefined rule sets / best-practice templates for various industries
Licensing and cost allocation only for effectively used modules
Rapid return on investment through smart role and authorisation management
Automates
Meets individual governance, risk and compliance (“GRC”) requirements
Reduces application risks in the Business Suite
Automates management, monitoring and reporting of the Business Suite
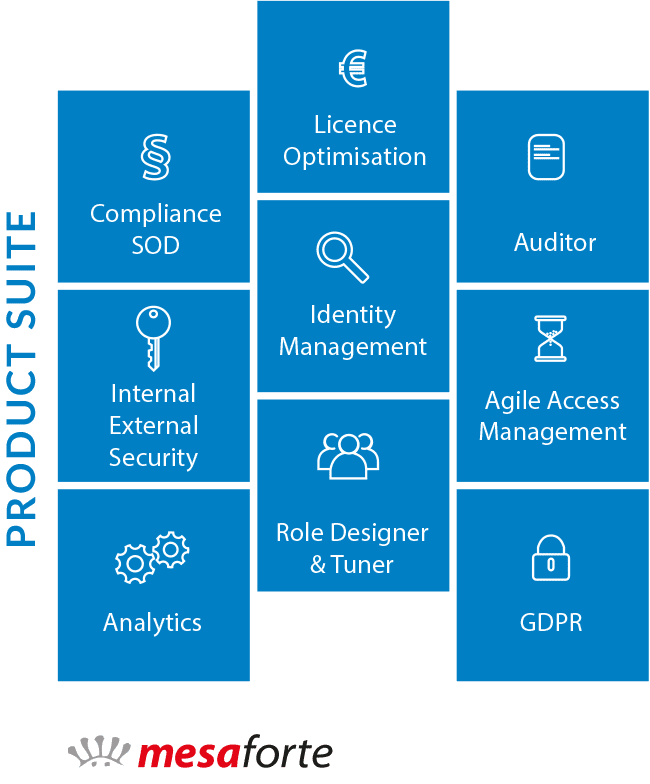
The 9 modules of the mesaforte.grc.suite
- Identity Management
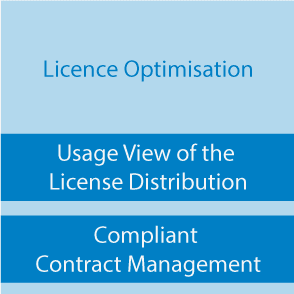
- Licence optimisation
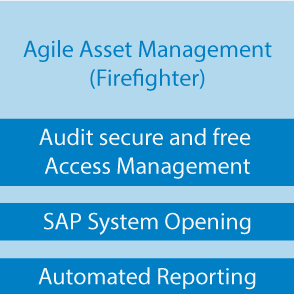
- Agile Access Management (“Firefighter”)
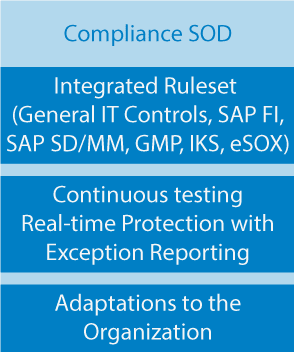
- Compliance / Segregation of Duties
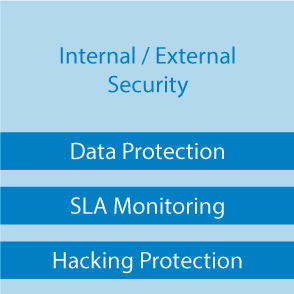
- Internal / External security
- Role Designer & Tuner
- Analytics
- Auditor
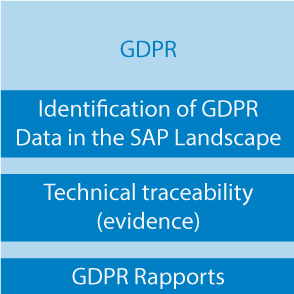
- GDPR

Automated management of SAP roles and their distribution
Efficient role management
Role design, role templates, organisational calibration, efficient role provisioning


Audit documentation and management
Internal, automated audit
Scope of audit; definition of audit chapters; audit with results & roadmap for implementation


Reduction of risks and automated logs
Risk reduction by means of temporary agile authorisations
Definition of agile access rights, calibration of temporary additional roles, deployment of temporary roles, audit of user logs

Data protection
Analysis and protection
Identification of data worth protecting; data access analysis, data protection measures, validation processes

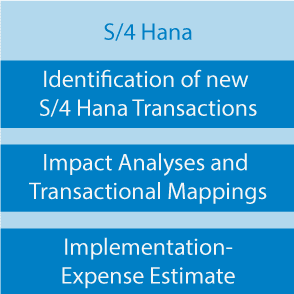
Readyness for secure, user-oriented S/4 Hana projects
Transaction impact and mapping of transactions from the old to the new S/4 Hana environment
Effort estimation for the implementation of S/4 Hana projects

Identify efficient internal SOD (Segregation of Duties) controls
SAP Rule Sets
“ready-to-go”
Rule Sets: SAP, ICS, eSOX; continuation of checks, real-time SOD check, risk visualisation; organisational calibration

Identify general IT control risks
Real-time protection through automated controls
Rules Set General IT Controls; SLA Monitoring, Hacking Protection

Create transparency
User transparency and process visualisation
Access and usage analysis
Efficient asset management
Cost-optimised licence management
Parameterisation User appropriate licence allocation; ROI calculation; Compliant contract management