The Shadow Data Risks Hiding in Your Supply Chain
In early June, news broke that data on 130,000 UBS employees had surfaced on the darknet – not because hackers broke through UBS’s own defences, but via a supplier: procurement service provider Chain IQ. UBS wasn’t alone. Several Chain IQ customers, including banks and major corporations, were caught in the fallout.
You probably read the news headlines describing this as a cyber-attack. But the deeper issue is one many organisations still overlook: Why did this supplier have access to such sensitive data in the first place?
And this is just one of a growing number of incidents exposing the hidden vulnerabilities created by third-party data relationships. Too often, senior leaders are not aware of how much sensitive information sits outside their direct control, scattered across a network of suppliers, vendors, and partners. This “shadow” data ecosystem can easily become a blind spot in many organisations’ governance strategies, leaving them exposed.
This is backed up by IBM’s 2024 Cost of a Data Breach Report, which revealed that 35% of breaches involved data stored in unmanaged sources – commonly known as “shadow data.” These breaches took 26.2% longer to identify and 20.2% longer to contain compared to breaches without shadow data. The result is not only higher immediate costs but also wider impacts long-term. Contractual disputes, legal action, and other downstream costs often continue to surface two to three years after the initial breach.
Then there are the unrealised implications that could happen even further in the future. Dr. Ilia Kolochenko, CEO of ImmuniWeb, told Infosecurity Magazine that the data stolen in the UBS breach could enable social engineering attacks impersonating bank employees, especially with the rise of sophisticated tools like deepfakes:
“The wide availability of GenAI tools, capable of impeccably impersonating voices and even videos, may certainly amplify the consequences of the data breach. Worse, some of the stolen data may be exploited to blackmail bank employees or even facilitate money laundering via sophisticated social engineering operations,” he said.
And it’s not just data privacy we must consider. Another recent case highlights how these risks can extend to operational resilience. In June 2024, UK logistics firm Peter Green Chilled – supplier to major supermarkets like Tesco, Sainsbury’s, and Aldi – fell victim to a ransomware attack. Although the company managed to keep its transport operations running, its ability to process orders was crippled. One of its customers faced the prospect of thousands of perishable food products going to waste. This shows how smaller supply chain players, often lacking robust cyber defences, can become single points of failure for larger businesses. It’s not just the size of the supplier that matters – it’s the strength of their governance and controls.
Who Owns the Mistake? Why Accountability Is the Missing Piece
If you’re familiar with our series of blog posts, you’ll know that good governance isn’t just about policies on paper – it’s about people and accountability.
For example there’s the case of the Swiss Air Force, whose sensitive documents were leaked on the dark-web after a cyber-attack on supplier, U.S. security firm Ultra Intelligence & Communications. The Swiss Air Force relied on this external company for critical technology and trusted them with sensitive defence information. But there’s often little visibility into the supplier’s own cybersecurity practices, especially when it comes to smaller vendors or niche providers.
There is also the common but risky practice of giving third-party suppliers permanent admin rights, which are often left in place for convenience. These risks typically arise not from malice, but from short-term decisions made for speed that overlook long-term consequences. As Gartner points out:
“Privileged access carries significant risk. Even with privileged access management tools in place, the residual risk of users with standing privileges remains high.”
Temporary access becomes permanent. “Technical users” are given privileges they shouldn’t have. No one is truly accountable for monitoring, restricting, or revoking that access over time.
The attack on Peter Green Chilled we mentioned earlier is another reminder that this problem extends beyond data breaches into operational disruption. When smaller suppliers are compromised, the downstream effects – whether that’s perishable goods going to waste or critical services grinding to a halt – highlight the urgent need for organisations to take shared responsibility for resilience across the entire supply chain. Without clear accountability and robust governance, businesses risk not only their data but their operations, reputation, customer trust and profit margins.
This is where robust GRC systems come in. Combining clear policies with software support allows organisations to:
- Assign responsibility for every data flow
- Enforce temporary access rights that expire automatically
- Monitor and log data movement in real time
- Ensure compliance with deletion and non-use policies
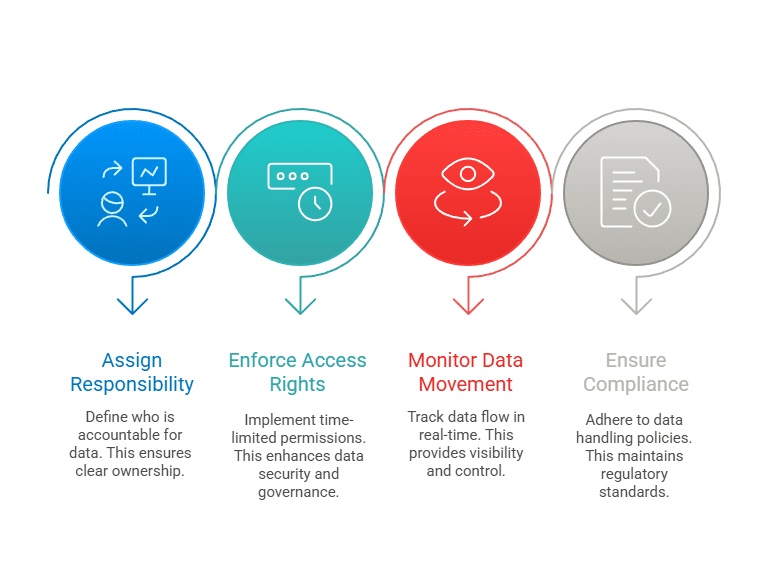
Without these controls, organisations are left in the dark – and when mistakes happen, accountability is often hard to pinpoint. And this is not a challenge to be ‘left for later’ as the longer these gaps persist, the harder they become to fix. Smart GRC not only closes these gaps but gives businesses the confidence to scale securely.
Closing the Loop – From Supplier Risk to AI Readiness
All these incidents have one thing in common: weak data oversight where you connect with external suppliers. And in a world where AI depends on clean, well-governed information, these cracks don’t just expose you to breaches – they undermine your entire digital strategy. Because good AI governance starts with knowing where your data is, who has access, and whether it can be trusted.
If AI is the engine of modern business, data is the fuel. But what happens when the fuel is contaminated or missing altogether?
As the OECD’s AI, Data Governance and Privacy Report 2024 highlights, this will remain an ongoing challenge for organisations investing in AI. Trustworthy AI depends on trustworthy data. Without high-quality, current, and well-governed information, AI systems falter. If sensitive data leaks, becomes outdated, or sits in the hands of third parties with weak controls, the value of AI falls – and the risks grow.
At the heart of this challenge are basic but often neglected GRC (Governance, Risk, and Compliance) questions:
- What data is shared externally?
- Why is it shared?
- For how long?
- Under what controls and with what oversight?
In many cases, these questions don’t get asked until something goes wrong. But with the right mix of automation, smart processes, oversight and accountability, organisations can reduce this complexity. Automated logging, clear access management, and strict deletion policies ensure that data is shared only when necessary, for as long as necessary, and always under tight control.
In short: if you don’t know where your data is, neither does your AI. And without trustworthy data, even the smartest AI can’t help you.
From Data Risk to Data Readiness – Your AI-Ready GRC Checklist
As your organisation evolves to embrace the opportunities of AI, shifting from a reactive stance to a proactive, prevention-first approach doesn’t just reduce risk. It creates value. Advanced AI algorithms can now analyse patterns in real-time data streams, identifying potential risks before they materialise. As Peter Miller, President and CEO of The Institutes pointed out:
“The best loss is the one that never happens.”
With the right GRC framework in place, organisations can:
- Reduce operational workload by automating manual controls
- Minimise complaints and disruptions by ensuring data quality
- Build trust with customers, partners, and regulators
- Lay the groundwork for AI systems that deliver real, reliable results
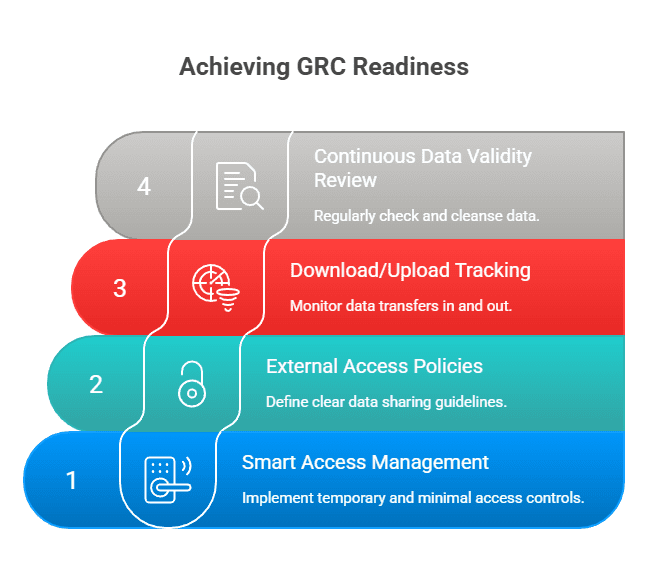
Here’s a quick GRC readiness checklist to get you started:
- Smart Access Management: Ensure external access is temporary, minimal, and automatically revoked when no longer needed.
- External Access Policies: Define clear policies for how and when data can be shared with third parties.
- Download/Upload Tracking: Implement systems to monitor all data transfers in and out of your organisation.
- Continuous Data Validity Review: Regularly check and cleanse your data to maintain accuracy and relevance.
At wikima4 our goal is to equip you with not only the tools, but also the knowledge to protect yourself and your data from avoidable disasters. In pursuit of this we’ve compiled a free white paper diving deeper into these steps, including practical tips for building AI-ready data governance without adding unnecessary complexity. Download it to learn how to turn your data risks into data readiness.
Embracing the world of AI can be both exciting and terrifying in equal measure. Trust is key, and while you might not be able to automate trust, you can build it in. And with wikima4 as your GRC Companion, we can help turn your data flow into a value stream.

