In today’s interconnected world, ERP systems power critical business functions – but what happens when a security gap brings everything to a standstill? The consequences can be devastating, ranging from data breaches to operational chaos.
ERP environments are the backbone of many organizations, enabling seamless operations across business processes. However, as these systems grow in complexity, so do the challenges of managing security, roles, and responsibilities. Unclear definitions and lack of collaboration can lead to inefficiencies, security vulnerabilities, and compliance risks. This article explores how organizations can strengthen their security by delivering effective training that enables teams to fulfil their roles, engage key stakeholders, and implement Data Access Governance Security (DAGS). By leveraging resources like wikima4, businesses can equip employees with the knowledge and skills needed to safeguard sensitive data, strengthen compliance, and ensure long-term ERP success.
Why Clearly Defined Roles Are the Cornerstone of ERP Success
In the intricate world of ERP environments, success hinges on more than just technology. It requires a clear and unified understanding of roles and responsibilities. Without this foundation, teams face operational bottlenecks, compliance risks, and security gaps. By defining responsibilities and fostering collaboration across organizational levels, businesses can create a robust security and compliance framework that bridges the divide between IT and business goals.
However, while role clarity supports overall ERP efficiency, it is particularly critical when it comes to security and compliance. Without well-defined security roles and structured access management, businesses expose themselves to data breaches, regulatory violations, and operational vulnerabilities. In the following sections, we will focus on how role clarity, stakeholder collaboration, and targeted training ensure a secure and compliant SAP environment.
Breaking Down ERP Role Complexity
Defining roles and responsibilities in ERP landscapes like SAP can be a daunting task. The complexity comes from a combination of technical and organizational challenges, such as siloed teams, overlapping responsibilities, and a lack of collaboration between departments. This often results in unclear ownership and decision-making processes.
Die Folgen unklarer Zuständigkeiten
When roles and responsibilities are undefined, inefficiencies permeate daily operations. Security gaps emerge, compliance risks escalate, and data access governance suffers. This is especially true in the context of security and compliance, where unclear responsibilities lead to excessive access rights, weak controls, and audit failures.
While individual teams may excel in their specific domains, the real challenge often lies in the interfaces between them. A lack of transparency and coordination between IT, business, security, and compliance teams can create blind spots, allowing risks to go unnoticed until they become serious vulnerabilities. Establishing clear ownership, defining accountability, and encouraging cross-functional collaboration are essential to bridging these gaps.
Establishing a Collaborative Authorisation Concept
A collaborative authorization concept ensures that priorities align across all organizational levels. By developing a clear and agreed-upon framework, stakeholders can avoid misunderstandings, streamline processes, and enhance system security. This alignment fosters mutual trust and accountability among business, IT, and compliance teams.
Key Stakeholders in an Authorisation Concept
So, strong security begins with clearly defined roles and collaborative effort. Now let’s talk about the key stakeholders involved in an authorization concept, their responsibilities, and the additional support required to ensure security, compliance, and operational efficiency.
Effective security relies on the involvement of all the key stakeholders.
Stakeholder Roles and Responsibilities Strategic Oversight:
- Senior Management: Provides strategic oversight, budget approval, and risk prioritisation.
- Project Managers: Oversee implementation and ensure collaboration.
Operational Implementation:
- IT Security Team: Implement security policies and monitor risks.
- SAP Basis Team: Manage technical aspects of roles and authorisations.
- SAP GRC-Team: Automate compliance checks and manage risk.
Compliance and Monitoring:
- Compliance and Audit Teams: Ensure regulatory compliance and conduct audits.
- Legal and Data Protection: Ensure data privacy and regulatory compliance.
Support and Enablement:
- Business Process Owners: Define access needs and validate role designs.
- Role Owners: Custodianship of roles and periodic reviews.
- Training Teams: Educate users and manage organizational change.
- End Users: Follow assigned roles and report security issues.
- External Consultants/Partners: Provide expertise and best practices.
Additional Support from Role Owners and External Consultants
Role custodianship is pivotal in ensuring that every user’s access is carefully managed and aligned with both operational and security and compliance requirements. Legal and data protection officers further strengthen the framework by upholding compliance with regulations and safeguarding sensitive data. Meanwhile, training and change management teams bridge the gap between strategy and execution, equipping stakeholders with the knowledge and tools necessary to adopt new frameworks effectively.
External consultants also play a crucial role in enhancing security and compliance. Their expertise helps organizations navigate complex regulatory landscapes, implement best practices, and optimize authorization models. Whether assisting in risk assessments, refining role designs, or providing targeted training, consultants bring valuable insights that support both strategic initiatives and day-to-day security operations.
When all these roles work in harmony, organizations lay the foundation for a robust, adaptable security model – one that not only protects critical systems but also builds a sense of trust and collaboration across the board.
Building Strong Foundations: The Six Steps to Data Access Governance Security (DAGS)
Imagine if your company was handling highly sensitive customer data in its ERP system, but no one had a clear policy on who could access it. One day, a staff member with minimal clearance accidentally accesses this data and unknowingly leaks it. The repercussions are immediate: trust in your company plummets, legal actions follow, and the financial damage is crippling. Now, imagine if a robust data access governance framework had been in place, clearly defining access rights and monitoring every touchpoint. With strong governance, this leak could have been prevented, and your data – and reputation – would have remained secure.
So, it seems clear, establishing strong data access governance is essential for safeguarding sensitive information and maintaining the integrity of ERP environments. Let’s now explore a framework that offers a structured approach to enhance agility, streamlined operations, and mitigating risks in real time.
What is DAGS and Why Does it Matter?
Data Access Governance Security (DAGS) ist ein wichtiger Rahmen für die Verwaltung des Zugangs und die Verbesserung der Sicherheit. Es konzentriert sich auf Flexibilität, betriebliche Effizienz und Echtzeit-Bedrohungserkennung zum Schutz sensibler Daten.
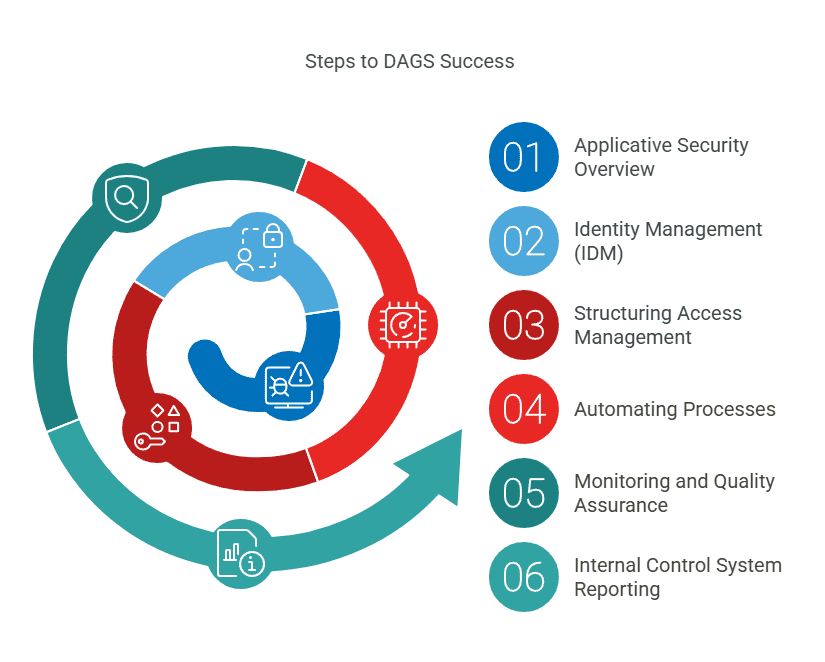
The Six Steps to DAGS Success
- Applicative Security Overview: Understand your system’s vulnerabilities and safeguards.
- Identity Management (IDM): Use IDM as the control centre for user access.
- Structuring Access Management: Define and assign responsibilities for access control.
- Automating Processes: Leverage automation for consistency and efficiency.
- Monitoring and Quality Assurance: Regularly assess security measures to ensure continuous improvement.
- Internal Control System Reporting: Enhance transparency and provide actionable insights.
How to Gain a Deeper Understanding of DAGS
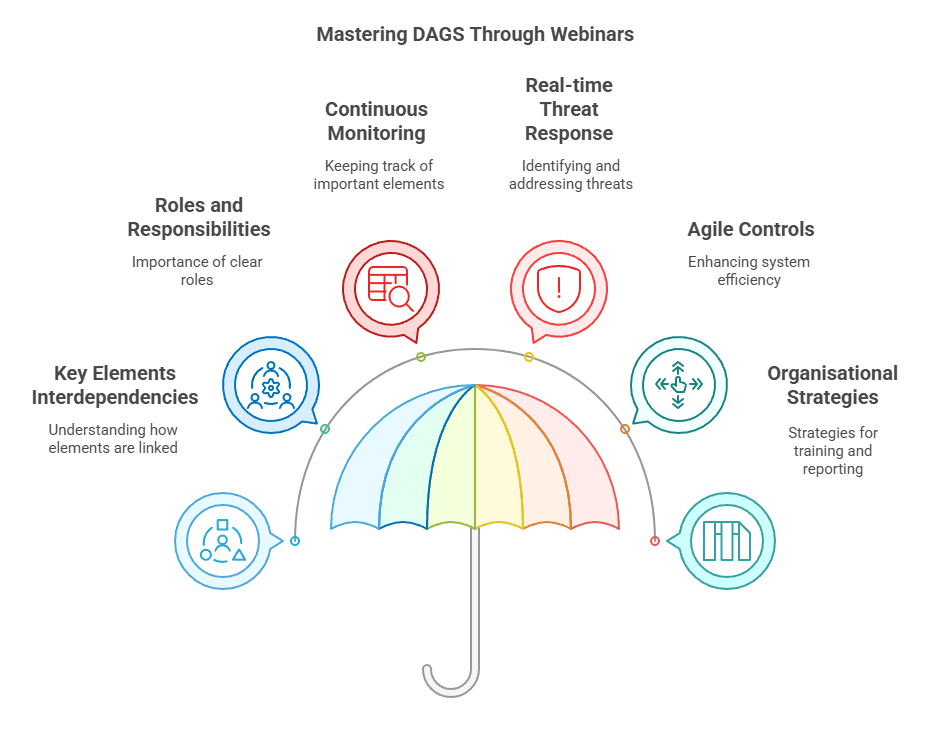
To help you master DAGS, wikima4 will host a webinar series in March and April. These 30-minute sessions will provide role-specific training and practical insights into implementing the six steps effectively. We will be covering the following topics:
- Understanding the relationship and interdependencies between key elements.
- Highlighting the importance of clearly defined roles and responsibilities.
- Learning why it is crucial to continuously monitor important elements in an ERP system.
- Identifying and responding to threats in real-time.
- Recognising how agile controls contribute to an efficient system.
- Exploring organizational strategies for training, documentation, and reporting within the company.
This webinar series is a fantastic tool to help you implement the six steps of DAGS and leverage role-specific training so you can fortify your security posture with confidence. A well-implemented DAGS framework is more than a technical solution – it’s a commitment to resilience, efficiency, and proactive threat management.
Training for Success: Equipping Stakeholders for Security Excellence
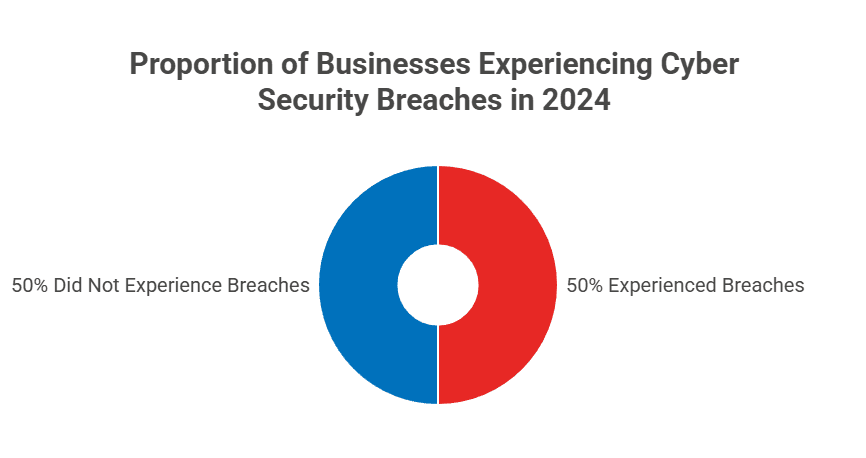
Most people are aware that training can improve one’s understanding and use of a product or strategy. But in the case of security, it’s important to remember how a lack of training can lead to disastrous consequences. The British Home Office reported that at least half of all businesses suffered from a cyber security breach in 2024, so it’s really more a question of WHEN than IF. You need to make sure your staff and managers are ready to act with a cool head when it happens.
Training serves as the critical link between strategy and action, ensuring that every stakeholder – whether it’s senior management, end users, IT teams, or auditors – plays their part in safeguarding your ERP system. By tailoring training to specific roles and fostering a culture of continuous learning, organisations can strengthen their defences, remain agile in the face of new threats, and maintain operational resilience.
Strategies for Effective Compliance and Security Training Delivery
To ensure security and compliance is seamlessly integrated across the organization, training should be tailored to meet the distinct needs of both business and IT stakeholders. A one-size-fits-all approach won’t be enough – effective training connects strategic objectives with practical implementation at every level.
- Senior Management (Business Stakeholders): Training should focus on strategic oversight, risk awareness and regulatory compliance to ensure that security and governance policies align with business goals.
- End Users (Business Stakeholders): Equip them with practical skills for daily system use while reinforcing data access governance (DAGS) principles, role-based restrictions, and adherence to security and compliance best practices.
- IT Teams (Technical Stakeholders): Provide in-depth training on technical security controls, system monitoring, threat detection, and compliance-driven access management to protect critical assets.
- Auditors and Compliance Officers: Ensure they are proficient in regulatory compliance requirements and capable of conducting thorough system reviews.
Comprehensive documentation, paired with a commitment to ongoing learning, is the foundation of a resilient ERP security framework. By investing in tailored training and building a culture of continuous improvement, you can safeguard your systems and adapt to emerging challenges with confidence.
Agile Teams: The Key to Resilient ERP Systems
For any forward-thinking business in this digital age agility isn’t just an advantage, it’s a necessity. Effective compliance and security training acts as the glue that unites teams across the organisation, growing a culture of collaboration and shared accountability. With a focus on thorough documentation, transparent reporting, and a commitment to continuous improvement, you can build the foundation for true operational resilience.
Continuous training is the cornerstone of agility, empowering teams to respond to threats in real time while maintaining system efficiency. By regularly updating training programs to address new challenges, you can not only protect your ERP systems but also future proof your operations, staying ahead of evolving risks and demands.
Bringing Responsibility and Training Together for ERP Security and Compliance Success
We hope this post has helped you see that clearly defined roles, active stakeholder engagement, robust DAGS implementation, and tailored training programs are essential for enhancing security and compliance. By adopting an integrated approach, you can strengthen your security posture, achieve compliance, and enhance operational efficiency. And the best time to start that journey is right now.
The path to security success begins with your next step – explore wikima4’s webinars, tools, and resources today to secure your ERP systems for tomorrow.

